GPON is a fiber-based access technology that utilizes a passive optical network architecture to connect multiple subscribers over a single fiber, enabling unprecedented bandwidth expansion and cost savings.The core of GPON technology lies in its highly efficient data transmission mechanisms and advanced network management capabilities, which make it an ideal platform for supporting modern high-speed communications.
GPON is the world’s most widely used and mature fixed access network technology, thanks to the GPON system has a series of key technologies to improve bandwidth performance and stability, we will analyze these key technologies.
Key Technology No. 1: Ranging
1. Why Ranging?
For the PON port of the OLT, the logical distance from different ONUs to the OLT is not equal, and the optical signals have different transmission times on the fiber, and arrive at each ONU at different moments. At the same time, the loop time delay (RTD: Round Trip Delay) also changes with time and environment. Therefore, collision conflicts may occur when ONUs send uplink data in TDMA mode (i.e., at the same moment, only one ONU among all ONUs under one PON port of OLT is sending data), as shown in the figure.
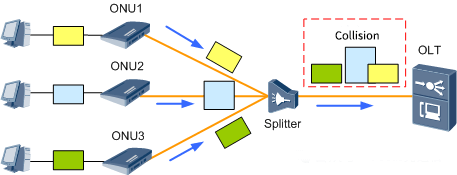
In order to ensure that the uplink data of each ONU is inserted into the specified time slot after fiber convergence without collision with each other and without too large a gap, the OLT must accurately determine the distance between each ONU and the OLT in order to control the moment at which each ONU sends uplink data.
2. How Ranging?
The process of ranging is as follows:
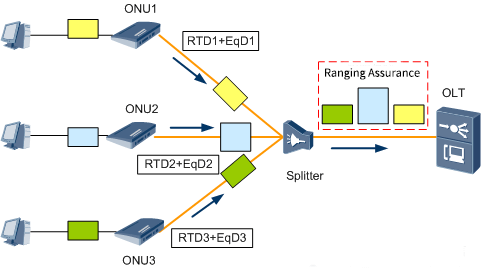
The OLT starts the ranging function when the ONUs are first registered, obtains the round-trip delay RTD of the ONUs, and calculates the physical distance of each ONU.
The appropriate equalization delay parameter EqD (Equalization Delay) is specified according to the physical distance of the ONU.
Note: The OLT needs to open a window, i.e., Quiet Zone, to pause the uplink transmission channel of other ONUs during the ranging process. The OLT opens the window by setting the BWmap to null and does not authorize any time slots.
3. What Are Tthe Results Of Ranging?
Through RTD and EqD, the data frames sent by each ONU are synchronized to ensure that each ONU does not generate conflicts at the backbone fiber when sending data.
It is equivalent to all ONUs sending data at the same logical distance and in the corresponding time slots, thus avoiding collision conflicts of uplink channels.
Key Technology No. 2: Burst Photovoltaic
GPON uplink direction using time-division multiplexing, each ONU must be in the licensed time slot to send data, does not belong to their own time slots must be strictly shut down the transmission signal of the optical module, so as not to affect the normal work of other ONUs.
For the OLT side of the uplink reception, it must be based on the time slot for the burst reception of each ONU uplink data, therefore, in order to ensure the normal operation of the GPON system, the ONU side of the optical module must support the burst transmission function, the OLT side of the optical module must support the burst reception function.
1. The ONU-side optical module must support the burst sending function

Ranging and ensure that different ONUs send the signal elements in the OLT side do not conflict with each other, but the ranging accuracy is limited, generally plus or minus 1bit, there will be a few bits of guard time between the signal elements sent by different ONUs (but not an integer multiple of the bit), if the ONU side of the optical module does not have the burst sending function, it will lead to the superposition of the transmitted signal, and the signal will be distorted.
2. The OLT side optical module must support the burst reception function

Since the distance from each ONU to the OLT is different, the optical signal attenuation is different for each ONU, so it may lead to different power levels of the messages received by the OLT in different time slots.
If the optical module on the OLT side is not equipped with fast processing of sudden changes in optical power, it will result in the optical signals of ONUs that are far away and have large optical power attenuation arriving at the OLT, and the wrong signals will be recovered due to the optical power level being less than the threshold (the signal is considered valid only if it is higher than the threshold level, and cannot be recovered correctly if it is lower than the threshold level).
Dynamic adjustment of the threshold function can be dynamically adjusted in the OLT in accordance with the strength of the optical signal received optical power threshold to ensure that all ONU signals can be completely restored.
Note: GPON downlink sends all data to the ONU side according to the broadcasting method, therefore, the optical module on the OLT side is required to emit light continuously, and the optical module on the ONU side also operates in the continuous receiving mode, so it is not necessary for the optical module to have the burst sending/receiving function.
Key Technology No. 3: DBA
In GPON systems, an efficient TDMA mechanism is required to control the uplink traffic so that packets from multiple ONUs do not collide during the uplink process. However, using a collision-based mechanism requires managing QoS in the passive ODN of the PON, which is physically impossible to achieve or requires suffering a severe loss of efficiency. In turn, GPON considers the OLT software perspective, which is DBA.
DBA (Dynamically Bandwidth Assignment) monitors PON congestion in real time, and OLT dynamically adjusts bandwidth based on congestion and current bandwidth utilization, as well as configuration.
1. The Working Principle Of DBA
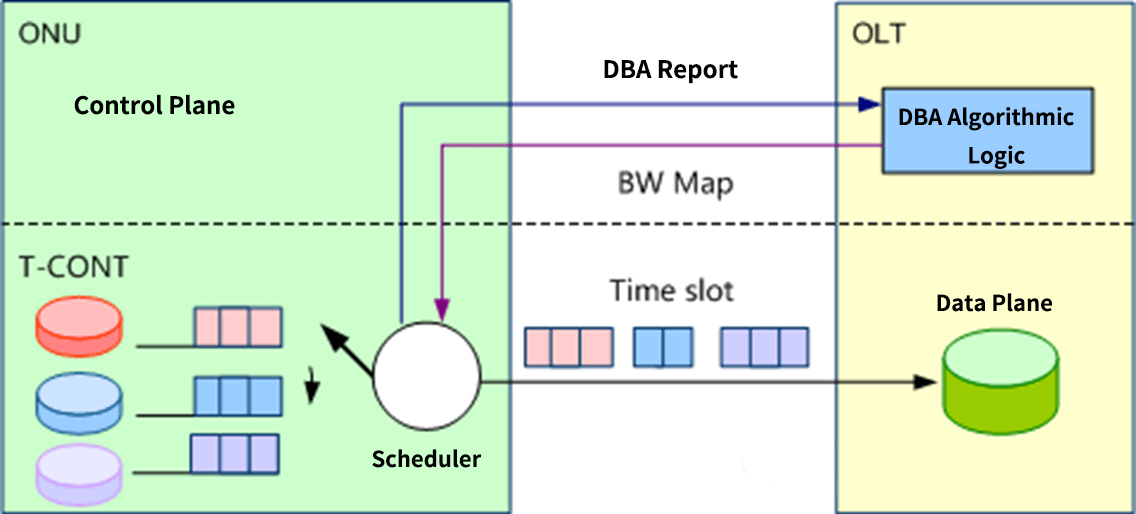
The ONU will report the status of the data queue cached in its own T-CONT based on the DBA request information sent to the OLT.
The internal DBA module of the OLT continuously collects the DBA report information from each ONU, performs calculations, and sends the results of the calculations down to each ONU in the form of a BW Map.
Each ONU sends uplink burst data in its respective time slot according to the BW Map information, occupying the uplink bandwidth. This ensures that each ONU can dynamically adjust the uplink bandwidth according to the actual sent data traffic, which improves the utilization of the uplink bandwidth.
2. DBA Functions
The GPON system can realize the following functions by introducing DBA:
- Increase the uplink line bandwidth utilization of PON ports
- More users can be added to the PON port
- Users can enjoy higher bandwidth services, especially for services with relatively large bandwidth variations
Key Technology No. 4: FEC
1. Why Does PON Need FEC?
The main reason for using FEC technology in PON systems is to improve the transmission quality and reliability of the line. Specifically, FEC technology can reduce the BER at the receiving end, increase communication stability, avoid data retransmission, improve bandwidth utilization and reduce retransmission rates. In addition, FEC technology can reduce the demand for high-performance optical devices, thereby reducing equipment costs.
The FEC algorithm used in the widely used GPON system is the RS (255, 239) algorithm, which fully complies with the requirements of ITU-T G.884.3.
In the RS (255, 239) algorithm, the input data is treated as a vector of length 239, which is encoded to produce a vector of length 255. Each element of this coded vector is an error-correcting code element, which consist of 239 information bytes and 16 checksum bytes from the input data. Each of these 255 code elements can correct up to 8 bytes of errors.
Specifically implemented, the GPON system FEC function can be turned on and off separately for uplink and downlink for each ONU; the ONU equipment can support adaptive reception of downlink service streams with and without FEC coding.
Downlink direction:
OLT: Either FEC coding or no FEC coding is applied to the downlink data; the specific coding status is identified using an intra-frame field and sent to the ONU.
ONU: Each ONU is able to FEC decode the received data or not (even if the data is encoded). By using block-based RS coding, the location of the checksum bits can be known in advance. In this way, ONUs that do not support FEC can skip the checksum bits, i.e., they are not processed and the raw downlink data is available without FEC decoding.
Uplink Direction:
ONU: Each ONU may either use FEC to encode its uplink data or not; the specific encoding status will be identified using an in-frame field.
OLT: It must be possible (for each ONU transmission) to receive uplink data with or without FEC decoding (even if it is FEC encoded).
2. How exactly is FEC implemented in GPON?
After saying so much above, maybe you are still not very clear. So next, let’s take the FEC coding of downlink frames in GPON system as an example to explain.
When FEC coding is used for downlink frames, the FEC checksum byte is inserted at the end of each code word. Then when RS (255, 239) is used, each 239 data byte is followed by 16 checksum bytes. The PCBd portion of the frame is included in the first code word, that is, the code word starts at the first byte of the frame. The next code word begins after the 255th byte and repeats every 255 bytes.
Note that since the bit rate of the downlink is not increased, the FEC checksum byte is inserted into the stream instead of the data byte. As a result, the effective bandwidth for user data is reduced when FEC is used. (The FEC coding process is performed prior to scrambling)
Among them, we find a short code word at the end, which we sometimes call the shorter tail code word. Since the downlink frame is divided into 255 byte code words, when using 125us frames, the data in the last code word will be less than 255 bytes, and in turn there is a corresponding processing mechanism for this tail code word, i.e.:
- In order to make the number of bytes in the tail code word is equal to 255, before the encoding of the method of complementary “0” will be supplemented to 255 bytes
- Calculate the checksum byte
- The supplementary “0” byte is deleted, and the shorter code word is transmitted
- When the receiver receives, the same method of adding “0” is used to add the last code word to 255 bytes
- After decoding, the “0” byte is deleted again
For a downlink data rate of 2.488 Gbps, the frame length is 38,880 bytes. Since only 120 bytes are reserved for the trailing code word, 104 bytes are used as data bytes, 16 bytes are used as checksum bytes, and 135 bytes are padded with “0”.
Key Technology No. 5: Line Encryption
The downlink data in the GPON system is sent to all ONUs by broadcasting, so that the illegally accessed ONUs can receive the downlink data from other ONUs, which is a security risk. Therefore, GPON system adopts line encryption technology to solve this security problem.
GPON system adopts AES-128 encryption algorithm to encrypt data messages transmitted in plaintext and transmit them in ciphertext to improve security.
The GPON system performs AES key exchange and update periodically to improve line data reliability.
- The OLT initiates a key replacement request, and the ONU responds and sends the generated new key to the OLT
- The OLT receives the new key, performs key switching, and encrypts the data using the new key
- The OLT notifies the ONU of the frame number using the new key via the relevant command
- The ONU receives the frame number with the new key and switches the checksum key on the corresponding data frame
Due to the limited length of the PLOAM (Physical Layer OAM) message, the key is sent to the OLT in two parts and repeated three times. If the OLT does not receive any of the three transmissions, the OLT will resend the key replacement request until the same key is received three times.
The OLT notifies the ONU of the frame number on which the new key is to be used using the relevant command, which is repeated three times. As soon as the ONU receives it once, the ONU switches the checksum key on the corresponding data frame.
Note: The encryption algorithm used in the GPON system does not add additional overhead and has no impact on bandwidth efficiency. the encryption used in the GPON system is turned on and does not result in an increase in transmission latency.
Concluding Remarks
Ranging, Burst Optical, DBA, FEC, and Line Encryption are five key GPON technologies that are beneficial to our understanding, application, and later deployment of passive networks. If you want to know more about GPON in PON networks, please refer to the guide GPON Technology Tutorial for more details.
As a manufacturer of passive fiber optic connectivity solutions, Bonelinks not only provides reliable pre-terminated fiber optic patch cords, but also produces low-loss fiber optic splitters to meet the link requirements of different equipment connection lengths, ports and overall loss values. If you have any confusion about GPON technology, please feel free to contact us to solve the problems encountered in network operation and maintenance.




